Receive Verification Emails Without Using Your Real Email
How to Receive Verification Emails Without Using Your Real Email
In the current digital landscape, confirming accounts via email is a standard security procedure. Nonetheless, numerous users are reluctant to share their actual email addresses due to privacy concerns.
Consequently, it is vital to understand how to receive verification emails without disclosing your real email address. This detailed guide examines practical methods, helpful tools, and best practices to assist you in handling verification tasks smoothly and securely.
Understanding the Need for Alternative Email Solutions
Initially, it is crucial to recognize the advantages of not using your actual email address:
• Safeguard Your Privacy: Keep your personal email hidden from potential spam or harmful entities.
• Decrease Spam: Reduce the number of unwanted emails invading your main inbox.
• Preserve Anonymity: Remain anonymous when signing up for various platforms or services.
Despite the aforementioned advantages, receiving verification emails without showing your primary email can be difficult, particularly if the platform requires real email addresses. Fortunately, there are several effective solutions to address this issue.
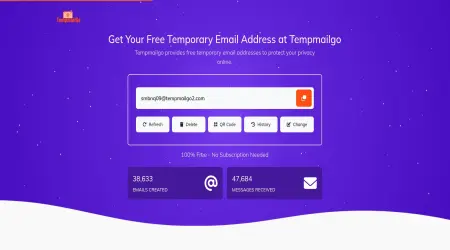
Utilizing Temporary Email Services
Temporary email services, occasionally referred to as disposable email providers, allow you to create a short-term email address instantly. These services are specifically designed to receive verification emails without compromising your actual account.
Popular Temporary Email Services
• Burner Mail: Provides customizable disposable emails and allows continued access if necessary.
• Guerrilla Mail: Offers temporary, anonymous email addresses that last for 60 minutes.
• 10 Minute Mail: Generates a temporary email that expires after ten minutes.
• ThrowAwayMail: Creates random email addresses with a more extended lifespan.
• Mailinator: Features public inboxes accessible by anyone, suitable for uses that are not confidential.
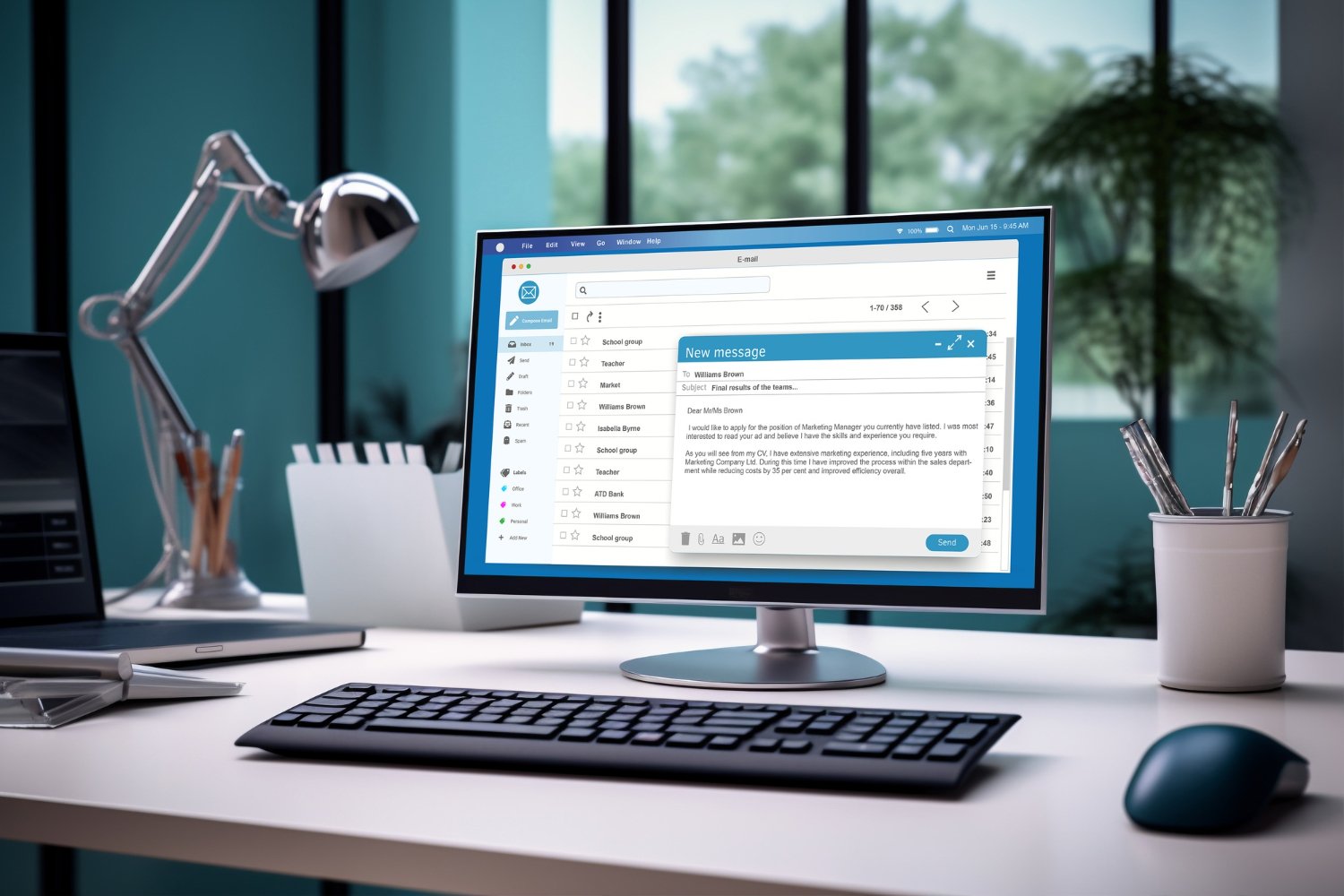
How to Use Temporary Email Services
1. Choose a reliable temporary email provider according to your requirements.
2. Instantly generate a new email address with a single click.
3. Copy the generated email address.
4. Input this email when you are asked to during registration or verification.
5. Access your temporary inbox via the provider’s website.
6. Find the verification email and click the confirmation link in the provider’s interface.
Note: When utilizing these services, always verify that the platform you are registering for doesn’t require long-term access, as temporary emails are typically deleted after a set duration.
Leveraging Email Aliases
Numerous email services, such as Gmail and Outlook, allow aliases—additional email addresses linked to your main account. These aliases can function as useful tools for verification without exposing your primary email.
Benefits of Email Aliases
• Simple Management: All messages go to your main inbox, making organization easier.
• Controlled Exposure: Use distinct aliases for different platforms, facilitating monitoring or deactivation.
• Improved Privacy: Hide your main email address from outside parties.
Creating and Using Aliases
• Gmail: Append "+alias" to your email address (for instance, username+platform@gmail.com). Emails sent to the alias will appear in your primary inbox.
• Outlook: Set up new aliases via your account settings and use them during sign-ups.
Setting Up a Dedicated Verification Email Account
If continuous verification is required, think about establishing a distinct email account specifically for this function.
This account ought to:
• Be Secured with a Password: Choose a robust and unique password.
• Feature Multi-Factor Authentication: To enhance security measures.
• Be Frequently Checked: Review this account on a regular basis for incoming verification messages.
• Remain Distinct from Personal and Work Accounts: To protect privacy and prevent disorganization.
Utilizing Email Forwarding and Filters
To simplify the handling of verification emails:
• Create filters that automatically categorize or relocate verification emails for easier access.
• Implement forwarding settings to send verification messages to your primary inbox or a specific folder.
• Certain email providers offer temporary forwarding links, which can aid in managing verification processes.
Recommended Practices and Security Suggestions
To improve efficiency and safeguard your privacy, follow these recommendations:
• Steer Clear of Public Email Services for Sensitive Verification: Choose secure and private alternatives.
• Exercise Caution with Permanent Email Aliases: Remove or deactivate aliases once verification is completed.
• Refrain from Sharing Sensitive Data via Disposable Emails: These are inappropriate for confidential information.
• Confirm the Reliability of Your Email Provider: Utilize trustworthy services to avert data breaches or leaks.
Overview
Receiving verification emails without disclosing your actual email address is entirely achievable through the use of different tools and tactics. Temporary email solutions are ideal for quick, one-time verifications. At the same time, email aliases offer long-term options for easy management. Establishing dedicated accounts and employing filtering methods further optimize the procedure. Always prioritize security and privacy to ensure your protection at every stage.
Final Reflections
In summary, by implementing these flexible methods—spanning from disposable email options to custom aliases—you can effectively safeguard your privacy. These strategies allow for smooth completion of verification procedures without compromising your primary email. Additionally, they help you maintain control over your digital presence while benefiting from the ease of receiving necessary verification emails. Therefore, consider these alternatives today to enhance your online privacy protection practices.

